This post describes how to configure a Cisco IOS Router with WebVPN. Cisco ISE (v2.1) will be used as a RADIUS server, to provide authentication and authorization. For testing purposes group membership will be used to determined which RADIUS attributes will be pushed to the connecting client.
RADIUS Server Configuration
For authorization Admin users will be permitted to use split tunnel, these configuration settings will be controlled centrally and pushed to the clients if they pass authorization.
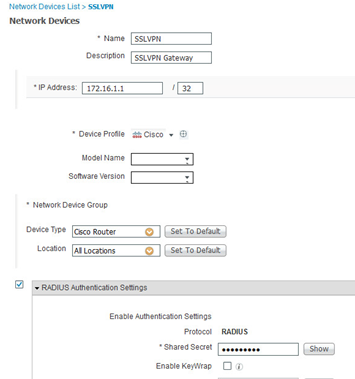
Define Network Device
Add the Router as a Network Device, ensure to enter the shared secret password, this must match the shared secret configured on the router.
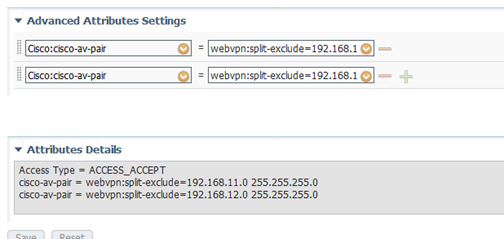
Create an Authorization Profile
- Configure a new Authorization Profile called “WebVPN Split Tunnel“
- Select “Advanced Attributes Settings”
- Select “Cisco:cisco-av-pair” and type “webvpn:split-exclude=IP ADDRESS SUBNET MASK”
Create Policy Set
- Create a new ISE Policy Set called “IOS SSLVPN”
- Match condition of the “NAS-IP-Address” of the Router
- Create new Authorization rules.
- For Admin Users select the Authorization Profile “WebVPN Split Tunnel” for the permissions to be returned
-
For all other users the default permission “PermitAccess”

IOS Router Configuration
Upload AnyConnect Client software
The AnyConnect Client image for each Operating System (Windows, Linux, Mac OS etc) must be uploaded to the Headend router in order for the device type to connect. Download the PKG file from the Cisco website
Using TFTP or SFTP copy the PKG file to a folder called webvpn on the flash of the router

The AnyConnect must now be installed.
webvpn install svc flash:/webvpn/anyconnect-win-4.2.01022-k9.pkg sequence 1

Create PKI Trustpoint and generate RSA keypair
Create a RSA Keypair
ip domain-name lab.net
crypto key generate rsa label SSLVPN_KEY modulus 2048
Configure a PKI Trustpoint in order to enrol the router with a certificate
crypto pki trustpoint LAB_PKI
enrollment mode ra
enrollment terminal
serial-number none
fqdn sslvpn.lab.net
ip-address none
subject-name cn=sslvpn.lab.net,ou=IT,O=LAB,ST=London,c=GB
revocation-check none
rsakeypair SSLVPN_KEY
Authenticate the certificate to download the Root Certificate and Enroll to create a local certificate for the router
crypto pki authenticate LAB_PKI
crypto pki enroll LAB_PKI
Configure RADIUS and AAA
A RADIUS server will be defined for authentication, authorization and accounting
aaa new-model
!
radius server ISE2
address ipv4 192.168.10.21 auth-port 1812 acct-port 1813
key Cisco1234
!
aaa group server radius ISE
server ISE2
!
aaa authentication login SSLVPN group ISE
aaa authorization network SSLVPN group ISE
aaa accounting network SSLVPN start-stop group ISE
Configure IP Address Pool
Create a local IP address Pool for VPN clients
ip local pool VPN_POOL 172.16.0.10 172.16.0.100
Configure Tunnel Interface
Create a loopback interface and reference within the Virtual Template
interface loopback0
ip address 172.16.1.1 255.255.255.255
interface virtual-template 1
ip unnumbered lo0
Configure WebVPN
Configure the WebVPN gateway to define the Public IP address, the listen ports, http redirection, define the previously create PKI Trustpoint and enable the WebVPN gateway
webvpn gateway SSLVPN_GATEWAY
ip address 1.1.1.3 port 443
http-redirect port 80
ssl trustpoint LAB_PKI
inservice
The WebVPN context is used to call the defined Group Policy, the context can also be used to customise the web portal
webvpn context SSLVPN_CONTEXT
ssl authenticate verify all
The Group Policy defines the local IP Address Pool, DNS Server, AAA list, Virtual Template settings to be used
policy group SSLVPN_POLICY
functions svc-enabled
svc address-pool "VPN_POOL" netmask 255.255.255.0
svc dns-server primary 192.168.10.5
virtual-template 1
default-group-policy SSLVPN_POLICY
aaa authentication list SSLVPN
gateway SSLVPN
inservice
Verification
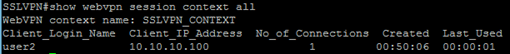
The command show webvpn session context all will show all connected sessions
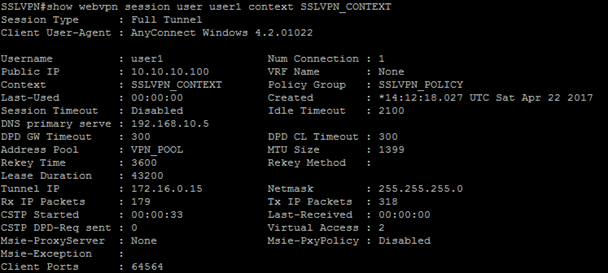
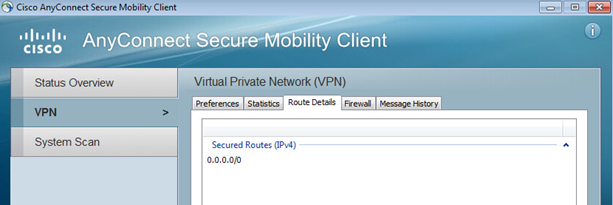
The command show webvpn session user USERNAME context all will show the specific user session. Notice in the screenshot below this user must be an “Admin User” as the previously configured split tunnel subnets have been applied to this session.

This can be confirmed on the client end

Logging in as a normal user (not an admin) will reveal no split tunnel subnets.
The ISE logs will also show what Authorization Profile has been applied to a session

Reference
For further information on using RADIUS AV (attribute-value) pairs with WebVPN
Click to access sec-conn-sslvpn-15-mt-book.pdf