The intention of this blog post is to describe the steps to configure certificate authentication for FlexVPN on a Cisco IOS router. This post will not describe all the steps to enrol for a certificate or all the steps to configure FlexVPN, refer to the previous blog posts list below.
The configuration used is based on the FlexVPN sVTI blog post below and has successfully enrolled for certificates on all routers. VPN connectivity has been established using PSK, the configuration below will convert from PSK to certificate authentication.
References
Requesting a certificate on Cisco IOS router using SCEP or manual enrolment
Configuring FlexVPN VTI and Hub-and-Spoke on Cisco routers.
Configure FlexVPN for Certificate Authentcation
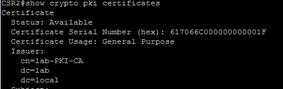
All certificates in this FlexVPN lab are signed by the CA called lab-PKI-CA
Run the command show crypto pki certificates to identify the issuer, in this instance lab-PKI-CA
Create a certificate map to match the name of the root certificate issuer-name
crypto pki certificate map CERT_MAP 5
issuer-name co lab-pki-ca
Configure the IKEv2 Profile to match the peers certificate issued by the CA defined in the Certificate map, specify the authentication local and remote to be rsa-sig, specify the local identity as the local router’s dn and identify the local trustpoint.
crypto ikev2 profile IKEV2_PROFILE
match certificate CERT_MAP
identity local dn
authentication local rsa-sig
authentication remote rsa-sig
pki trustpoint LAB_PKI
If you already have a tunnel up using PSK authentication, bounce the tunnel.
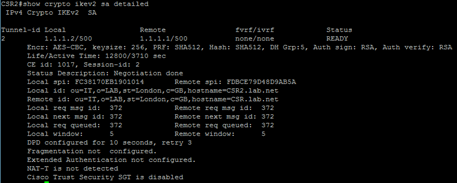
Run the command show crypto ike sa detailed to confirm IKEv2 sa have been established and authenticated using an rsa certificate
FlexVPN with Certificate Authentication Full Configuration
IKEv2 smart defaults have been used, which is why no IKEv2 proposal appears in the running configuration. Refer to this post for information about IKEv2 smart defaults
crypto pki trustpoint LAB_PKI
enrollment terminal
serial-number none
fqdn CSR2.lab.net
ip-address none
subject-name OU=IT,O=LAB,ST=London,C=GB
revocation-check none
rsakeypair VPN_KEY
auto-enroll 30 regenerate
!
crypto pki certificate map CERT_MAP 5
issuer-name co lab-pki-ca
!
crypto ikev2 profile IKEV2_PROFILE
match certificate CERT_MAP
identity local dn
authentication local rsa-sig
authentication remote pre-share
authentication remote rsa-sig
pki trustpoint LAB_PKI
lifetime 12800
dpd 10 3 periodic
!
crypto ipsec profile IPSEC_PROFILE
set ikev2-profile IKEV2_PROFILE
!
interface Loopback0
ip address 172.21.0.2 255.255.255.255
!
interface Tunnel1
ip unnumbered Loopback0
tunnel source GigabitEthernet1
tunnel destination 1.1.1.1
tunnel protection ipsec profile IPSEC_PROFILE
6 thoughts on “FlexVPN with Certificate authentication”